+8
.github/workflows/deploy.yaml
+8
.github/workflows/deploy.yaml
···
-1
README.md
-1
README.md
···
+112
-26
flake.lock
+112
-26
flake.lock
·······································
+7
flake.nix
+7
flake.nix
·········
+68
-2
machines/atalanta/home/default.nix
+68
-2
machines/atalanta/home/default.nix
······
+1
machines/atalanta/home-manager.nix
+1
machines/atalanta/home-manager.nix
+5
machines/ember/default.nix
+5
machines/ember/default.nix
······
-35
machines/john/default.nix
-35
machines/john/default.nix
···
-2
machines/moonlark/home/default.nix
-2
machines/moonlark/home/default.nix
+1
machines/moonlark/home-manager.nix
+1
machines/moonlark/home-manager.nix
+5
machines/nest/default.nix
+5
machines/nest/default.nix
······
+7
-2
machines/prattle/home/default.nix
+7
-2
machines/prattle/home/default.nix
···
+1
machines/prattle/home-manager.nix
+1
machines/prattle/home-manager.nix
+1
machines/tacyon/default.nix
+1
machines/tacyon/default.nix
+4
-2
machines/terebithia/home/default.nix
+4
-2
machines/terebithia/home/default.nix
······
+1
machines/terebithia/home-manager.nix
+1
machines/terebithia/home-manager.nix
+23
-1
modules/home/apps/bore/default.nix
+23
-1
modules/home/apps/bore/default.nix
···+labels=$(${pkgs.gum}/bin/gum choose --no-limit --header "Labels (select multiple):" "dev" "prod" "custom")···
+183
modules/home/apps/ssh.nix
+183
modules/home/apps/ssh.nix
···
-85
modules/home/apps/vscode.nix
-85
modules/home/apps/vscode.nix
···
-26
modules/home/system/nixpkgs.nix
-26
modules/home/system/nixpkgs.nix
···
+26
modules/home/system/nixpkgs.nix.disabled
+26
modules/home/system/nixpkgs.nix.disabled
···
+9
-2
modules/home/system/shell.nix
+9
-2
modules/home/system/shell.nix
·········
+32
modules/nixos/services/bore/README.md
+32
modules/nixos/services/bore/README.md
···+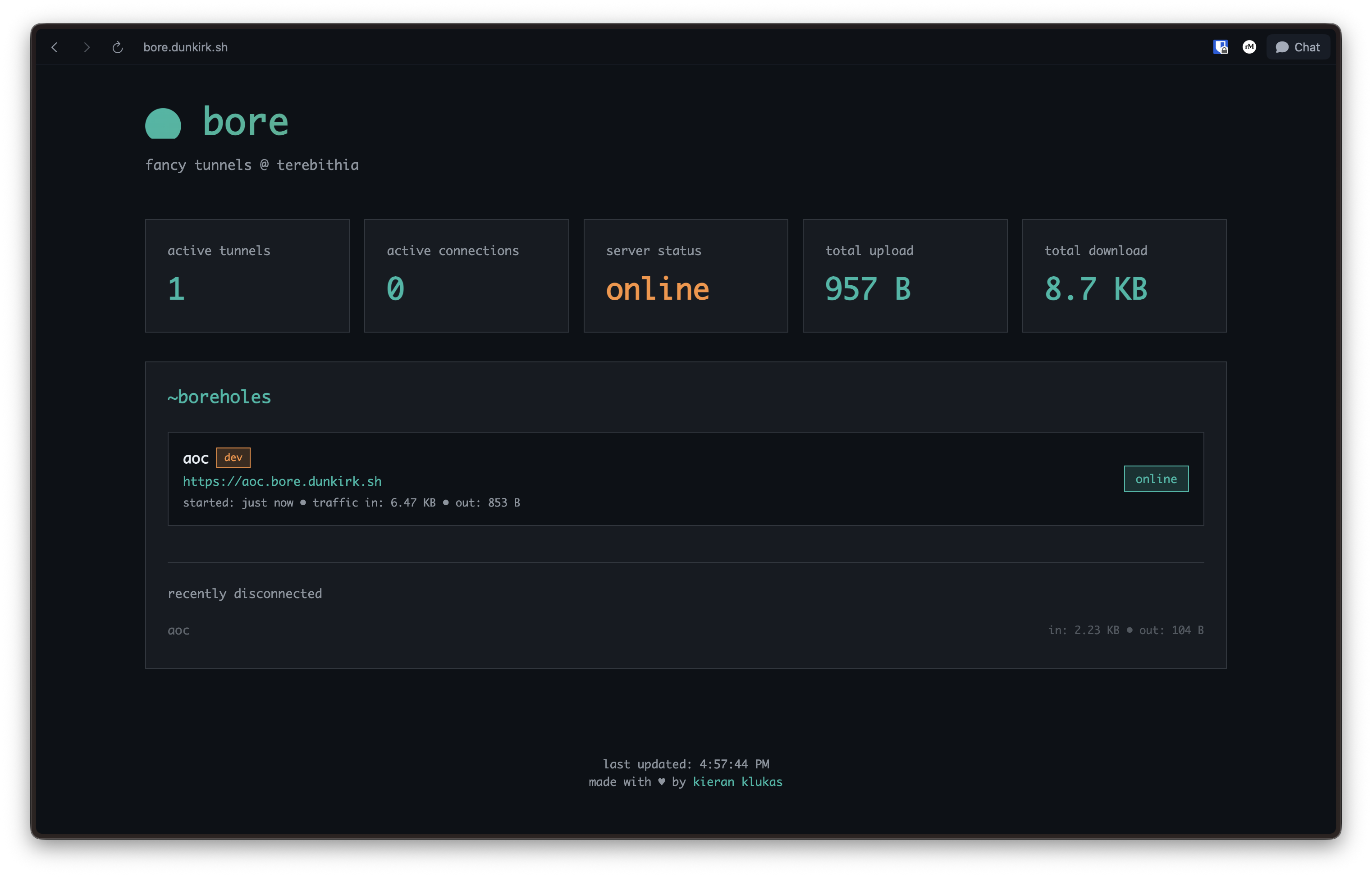+Bore is a lightweight wrapper around `frp` which provides a dashboard and a nice `gum` based cli. If you would like to run this in your own nix flake then simplify vendor this folder and `./modules/home/bore` and import the folders into the appropriate home manager and nixos configurations.+The secret file is just a oneline file with the key in it. If you do end up deploying this feel free to email me and let me know! I would love to hear about your setup!
-5
modules/nixos/services/bore/bore.nix
-5
modules/nixos/services/bore/bore.nix
···
+67
-12
modules/nixos/services/bore/dashboard.html
+67
-12
modules/nixos/services/bore/dashboard.html
·········+return `<span class="tunnel-label" style="color: ${style.color}; background: ${style.bgColor}; border-color: ${style.borderColor};">${trimmedLabel}</span>`;···html += '<div style="color: #8b949e; font-size: 0.85rem; margin-bottom: 0.75rem;">recently disconnected</div>';-<span class="offline-tunnel-name">${displayName || 'unnamed'}${label ? ` [${label}]` : ''}</span><span class="offline-tunnel-stats">in: <span data-traffic-in="${proxy.name}">0 B</span> • out: <span data-traffic-out="${proxy.name}">0 B</span></span>···-<span class="offline-tunnel-name">${displayName || 'unnamed'}${label ? ` [${label}]` : ''} → ${url}</span><span class="offline-tunnel-stats">in: <span data-traffic-in="${proxy.name}">0 B</span> • out: <span data-traffic-out="${proxy.name}">0 B</span></span>
+48
packages/zmx.nix
+48
packages/zmx.nix
···