+8
.github/workflows/deploy.yaml
+8
.github/workflows/deploy.yaml
···
-1
README.md
-1
README.md
···
+124
-38
flake.lock
+124
-38
flake.lock
···················································
+7
flake.nix
+7
flake.nix
·········
+4
machines/atalanta/default.nix
+4
machines/atalanta/default.nix
+73
-2
machines/atalanta/home/default.nix
+73
-2
machines/atalanta/home/default.nix
······
+1
machines/atalanta/home-manager.nix
+1
machines/atalanta/home-manager.nix
+5
machines/ember/default.nix
+5
machines/ember/default.nix
······
-35
machines/john/default.nix
-35
machines/john/default.nix
···
-2
machines/moonlark/home/default.nix
-2
machines/moonlark/home/default.nix
+1
machines/moonlark/home-manager.nix
+1
machines/moonlark/home-manager.nix
+5
machines/nest/default.nix
+5
machines/nest/default.nix
······
+7
-2
machines/prattle/home/default.nix
+7
-2
machines/prattle/home/default.nix
···
+1
machines/prattle/home-manager.nix
+1
machines/prattle/home-manager.nix
+1
machines/tacyon/default.nix
+1
machines/tacyon/default.nix
+9
machines/terebithia/default.nix
+9
machines/terebithia/default.nix
······
+4
-2
machines/terebithia/home/default.nix
+4
-2
machines/terebithia/home/default.nix
······
+1
machines/terebithia/home-manager.nix
+1
machines/terebithia/home-manager.nix
+131
modules/home/apps/bore/bore.1.md
+131
modules/home/apps/bore/bore.1.md
···+**bore** is a tunneling service that uses frp (fast reverse proxy) to expose local services to the internet via bore.dunkirk.sh. It provides a simple CLI for creating and managing HTTP, TCP, and UDP tunnels with optional labels and persistent configuration.+: The subdomain to use for the tunnel (e.g., "myapp" creates myapp.bore.dunkirk.sh). Must contain only lowercase letters, numbers, and hyphens.+Tunnel configurations can be saved to a **bore.toml** file in the current directory. This file uses TOML format and can be committed to repositories.+When running **bore** without arguments in a directory with bore.toml, you'll be prompted to choose between creating a new tunnel or using a saved configuration.
+38
modules/home/apps/bore/completions/bore.bash
+38
modules/home/apps/bore/completions/bore.bash
···
+21
modules/home/apps/bore/completions/bore.fish
+21
modules/home/apps/bore/completions/bore.fish
···
+42
modules/home/apps/bore/completions/bore.zsh
+42
modules/home/apps/bore/completions/bore.zsh
···
+490
modules/home/apps/bore/default.nix
+490
modules/home/apps/bore/default.nix
···+echo "$tunnels" | ${pkgs.jq}/bin/jq -r '.proxies[] | select(.status == "online" and .conf != null) | if .type == "http" then "\(.name) → https://\(.conf.subdomain).${cfg.domain} [http]" elif .type == "tcp" then "\(.name) → tcp://\(.conf.remotePort) → localhost:\(.conf.localPort) [tcp]" elif .type == "udp" then "\(.name) → udp://\(.conf.remotePort) → localhost:\(.conf.localPort) [udp]" else "\(.name) [\(.type)]" end' | while read -r line; do+${pkgs.gum}/bin/gum style --foreground 35 "✓ $current_tunnel → localhost:$port [$proto_display] [$label]"+${pkgs.gum}/bin/gum style --foreground 35 "✓ $current_tunnel → localhost:$port [$proto_display]"+${pkgs.gum}/bin/gum style --foreground 35 "✓ $current_tunnel → localhost:$port [$proto_display] [$label]"+${pkgs.gum}/bin/gum style --foreground 35 "✓ $current_tunnel → localhost:$port [$proto_display]"+saved_names=$(${pkgs.gnugrep}/bin/grep '^\[' "$CONFIG_FILE" | ${pkgs.gnused}/bin/sed 's/^\[\(.*\)\]$/\1/')+${pkgs.gum}/bin/gum style --foreground 35 "✓ Loaded from bore.toml: $tunnel_name → localhost:$port [$proto_display]''${label:+ [$label]}"+${pkgs.gum}/bin/gum style --foreground 196 "Invalid subdomain (use only lowercase letters, numbers, and hyphens)"+# Prompt for protocol if not provided via flag and not loaded from saved config and not already set+labels=$(${pkgs.gum}/bin/gum choose --no-limit --header "Labels (select multiple):" "dev" "prod" "custom")+if [ -f "$CONFIG_FILE" ] && ${pkgs.gnugrep}/bin/grep -q "^\[$tunnel_name\]" "$CONFIG_FILE"; then+admin_port=$(${pkgs.python3}/bin/python3 -c 'import socket; s=socket.socket(); s.bind(("", 0)); print(s.getsockname()[1]); s.close()')+${pkgs.gum}/bin/gum style --foreground 196 "Invalid protocol: $protocol (must be http, tcp, or udp)"+${pkgs.gum}/bin/gum style --foreground 214 "Connecting to ${cfg.serverAddr}:${toString cfg.serverPort}..."+proxy_status=$(${pkgs.curl}/bin/curl -s http://127.0.0.1:$admin_port/api/status 2>/dev/null || echo "{}")+remote_addr=$(echo "$proxy_status" | ${pkgs.jq}/bin/jq -r ".tcp[]? | select(.name == \"$proxy_name\") | .remote_addr" 2>/dev/null)+remote_addr=$(echo "$proxy_status" | ${pkgs.jq}/bin/jq -r ".udp[]? | select(.name == \"$proxy_name\") | .remote_addr" 2>/dev/null)
+183
modules/home/apps/ssh.nix
+183
modules/home/apps/ssh.nix
···
-85
modules/home/apps/vscode.nix
-85
modules/home/apps/vscode.nix
···
-26
modules/home/system/nixpkgs.nix
-26
modules/home/system/nixpkgs.nix
···
+26
modules/home/system/nixpkgs.nix.disabled
+26
modules/home/system/nixpkgs.nix.disabled
···
+9
-2
modules/home/system/shell.nix
+9
-2
modules/home/system/shell.nix
·········
+19
modules/nixos/services/battleship-arena.nix
+19
modules/nixos/services/battleship-arena.nix
···
+97
modules/nixos/services/bore/404.html
+97
modules/nixos/services/bore/404.html
···+href="data:image/svg+xml,<svg xmlns=%22http://www.w3.org/2000/svg%22 viewBox=%220 0 100 100%22><text y=%22.9em%22 font-size=%2290%22>🚇</text></svg>">
+48
modules/nixos/services/bore/README.md
+48
modules/nixos/services/bore/README.md
···+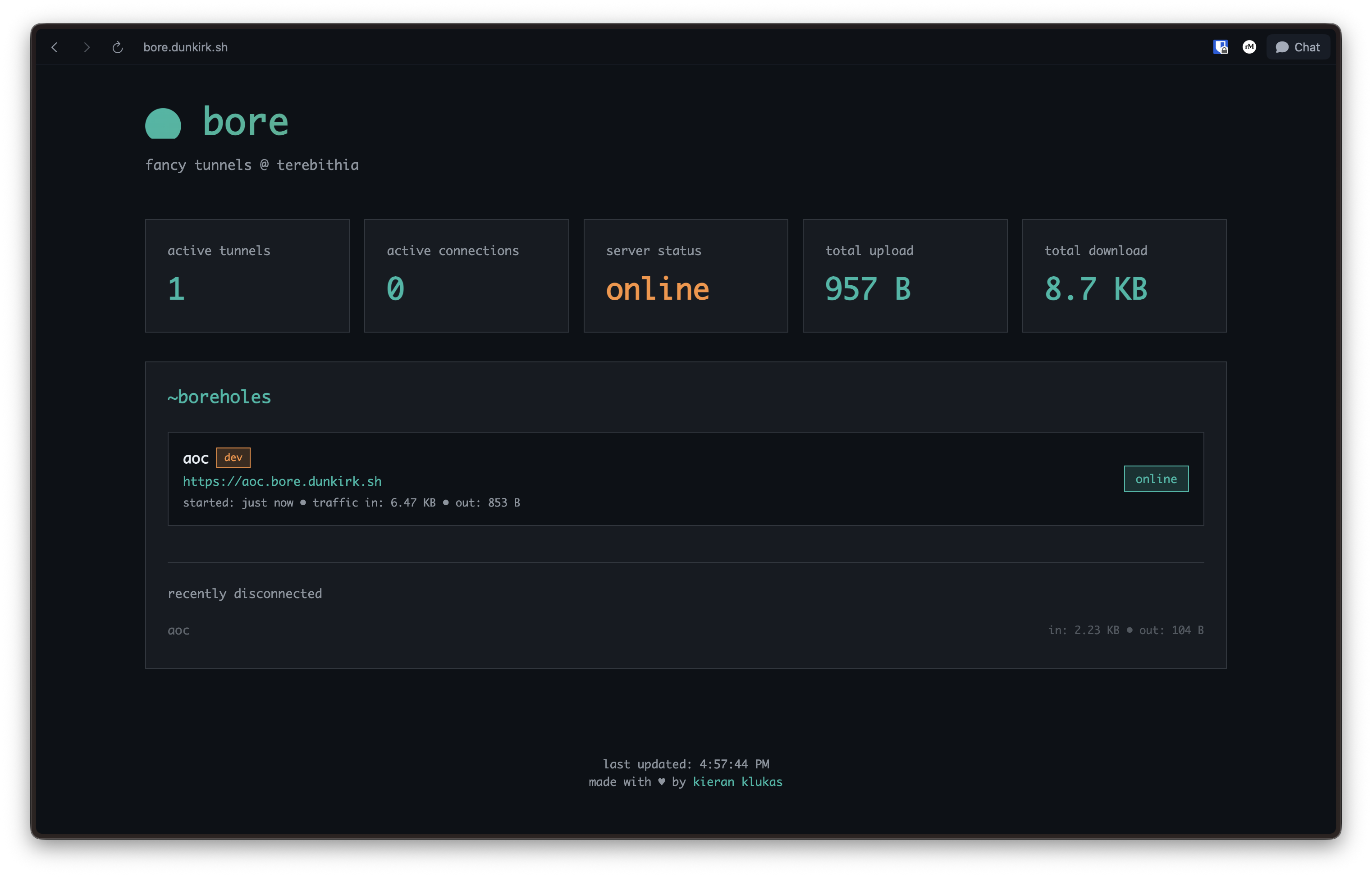+Bore is a lightweight wrapper around `frp` which provides a dashboard and a nice `gum` based cli. It supports HTTP, TCP, and UDP tunneling. If you would like to run this in your own nix flake then simplify vendor this folder and `./modules/home/bore` and import the folders into the appropriate home manager and nixos configurations.+The secret file is just a oneline file with the key in it. If you do end up deploying this feel free to email me and let me know! I would love to hear about your setup!
+190
modules/nixos/services/bore/bore.nix
+190
modules/nixos/services/bore/bore.nix
···
+24
modules/nixos/services/bore/bore.toml.example
+24
modules/nixos/services/bore/bore.toml.example
···
+626
modules/nixos/services/bore/dashboard.html
+626
modules/nixos/services/bore/dashboard.html
···+<meta name="description" content="bore - secure tunneling service for exposing local services to the internet">+<meta property="og:description" content="secure tunneling service powered by frp on bore.dunkirk.sh">+<meta name="twitter:description" content="secure tunneling service powered by frp on bore.dunkirk.sh">+href="data:image/svg+xml,<svg xmlns=%22http://www.w3.org/2000/svg%22 viewBox=%220 0 100 100%22><text y=%22.9em%22 font-size=%2290%22>🚇</text></svg>">+document.getElementById('totalUpload').textContent = formatBytes(serverData.totalTrafficOut || 0);+document.getElementById('totalDownload').textContent = formatBytes(serverData.totalTrafficIn || 0);+const totalTraffic = formatBytes((serverData.totalTrafficIn || 0) + (serverData.totalTrafficOut || 0));+return `<span class="tunnel-label" style="color: ${style.color}; background: ${style.bgColor}; border-color: ${style.borderColor};">${trimmedLabel}</span>`;+started: <span data-start-time="${proxy.lastStartTime || ''}"></span> • traffic in: <span data-traffic-in="${proxy.name}">0 B</span> • out: <span data-traffic-out="${proxy.name}">0 B</span>+html += '<div style="color: #8b949e; font-size: 0.85rem; margin-bottom: 0.75rem;">recently disconnected</div>';+<span class="offline-tunnel-stats">in: <span data-traffic-in="${proxy.name}">0 B</span> • out: <span data-traffic-out="${proxy.name}">0 B</span></span>+<span class="offline-tunnel-stats">in: <span data-traffic-in="${proxy.name}">0 B</span> • out: <span data-traffic-out="${proxy.name}">0 B</span></span>+const inputDate = new Date(now.getFullYear(), parseInt(month) - 1, parseInt(day), parseInt(hour), parseInt(minute), parseInt(second));
+48
packages/zmx.nix
+48
packages/zmx.nix
···
+13
secrets/frp-auth-token.age
+13
secrets/frp-auth-token.age
···